When researching cryptocurrencies, you’ve most likely come across the term “cryptography.” You might think cryptography is connected to cryptocurrencies in some way, and you would be correct.
However, cryptography is used for far more applications, such as data protection, ATMs, computer passwords, and much more. In this article, we walk you through the basics of cryptography and discuss its role in cryptocurrencies.
History of Cryptography
Cryptography is a method of hiding information to keep its content safe and secret. To uncover the information, the reader needs to know how the information has been modified, or encrypted. The encrypted message can, if properly done, be read only by the sender and the recipient.
Cryptography is far from new and has been around for thousands of years. Historically, cryptography was used to send important messages which were only meant for a select set of eyes. The first cryptographic messages were found on ancient Egyptians sites, but the first evidence for cryptography being used strategically dates back to the Roman era.
According to historians, Julius Caesar used cryptography, developing his so-called Caesar Cipher to send secret messages to his highest-ranking generals. This method of sheltering sensitive information from unwanted eyes has been used up until the modern era.
During World War II, the Germans used an encryption machine called the Enigma Machine to send important information to their ranks. As with most cryptography, there was a way to crack it, which was discovered by Alan Turing (mathematical genius and namesake of the Turing Test), now seen by some as one of the most decisive turning points in WWII.
The Basics of Cryptography
The abovementioned Caesar Cipher, or the shift cipher, is one of the simplest ways of encrypting a message and understanding cryptography. It is also called a shift cipher because it substitutes the original letters of a message with other letters by shifting up or down in the alphabet.
For instance, if we encrypt the message with +3, A would become D, and K would become N. Reversely, with a rule of -2, D would become B and Z would become X.
read everything on invest in blockchain
uhdg hyhubwklqj rq lqyhvw lq eorfnfkdlq
Even though this is one of the simplest cryptographic methods, the logic behind it is basically the same for each method. There is a message which is secret to everyone but the concerned parties, and a process to make this message unreadable for everyone except for those in the know. This process is the encryption, and it has two elements:
The Cipher – This is the set of rules that you’re using to encode the information. For example, shifting the alphabet an X number of letters like in the Caesar Cipher. The cipher doesn’t necessarily have to be a secret, because you will only be able to read it if you have access to the key.
The Key – This tells you how to arrange the set of rules of the cipher. For the Caesar Cipher, this would the the number of letters the cipher would alphabetically shift, such as +3 or -2. The key is the tool used for deciphering a message.
So a lot of people can have access to the same cipher, but without the key they are still unable to crack it.
The process for the transfer of a secret message goes as following:
- Party A wants to send a message to party B but wants nobody to read it.
- Party A uses a key to encrypt the message, transforming the text into a cipher text.
- Party B receives the cipher text.
- Party B uses the same key to decrypt the cipher text and can now read the message.
Advancements in Cryptography
Encrypted messages are encrypted to protect their content, which implies that there will always be parties interested in obtaining that information. However, as people have tried and succeeded in cracking various codes, cryptography has been forced to adapt. It has moved far beyond just shifting letters in the alphabet, evolving into extremely complex puzzles that are increasingly harder to solve. Instead of shifting a few letters in the alphabet, letters are now changed to numbers, other letters and symbols based on hundreds or thousands of intermediary steps.
The computer era led to an exponential increase in the difficulty of encryptions. This is because computers brought with them a drastic increase in computational power. The human brain is still by far the most complex computer around, but when it comes to doing calculations, computers are much faster and can handle far larger computations.
The cryptography of the digital era entails electrical engineering, computer science, and mathematics. Messages are now generally encrypted and decrypted using highly complex algorithms created by a combination of these technologies. However, no matter how strong the encryption, there will always be people working to crack it.
Cracking the Code
You can see that even without the key, a Caesar Cipher isn’t too hard to crack. Every letter can only take on 25 different values, and for most of the values the message will not make sense. By means of trial and error, you would be able to decipher the message without too much effort.
Cracking an encryption by trying all possibilities is known as brute force. It means trying all possibilities until a solution fits. With an increase in computing power, this becomes a more realistic threat which can only be tackled by increasing the complexity of the encryption. The more possible keys there are to a cipher, the more difficult it becomes to “brute force” your way to the message.
Current advanced ciphers allow for trillions of possible keys, making brute force less of a threat. However, it has been argued that supercomputers, and especially quantum computers, will soon be able to crack most encryptions through brute force because of their unmatched computational power.
As said, deciphering messages is becoming harder and harder, but it’s not impossible. This is because a cipher is inherently bound to a set of rules. The rules can be analyzed and give way to a more subtle way for decrypting a message: frequency analysis.
With the enormous increase in the complexity of ciphers, this can only be done through computers nowadays, but it can still be done. This technique analyzes recurring events and tries to find the key through this method.
Let’s use the Caesar Cipher example again to explain this. We know that the letter E is far more frequently used than other letters in the alphabet. When we apply this knowledge to a Caesar-encrypted message, we’re going to look for the letter that shows up most. We find that the letter H is used more often than others and test this assumption by applying a -3 shift to the message. The longer a message becomes, the easier frequency analysis becomes.
uhdg hyhubwklqj rq lqyhvw lq eorfnfkdlq
Cryptography and Cryptocurrencies
Most cryptocurrencies serve completely different purposes than sending secret messages, but cryptography still plays a key role. It has turned out that the traditional principles of cryptography and the tools used for it actually have more functions than we previously thought.
The most important newly discovered functions are hashing and digital signatures.
Hashing
Hashing is a cryptographic method for transforming large amounts of data into short numbers that are difficult to imitate. It is a key component of blockchain technology and is mainly concerned with the protection and integrity of the data flowing through the blockchain.
This method is mainly used for four processes:
- to verify and validate the account balances of wallets
- to encode wallet addresses
- to encode transactions between wallets
- to make the mining of blocks possible (for mineable cryptocurrencies) by creating the mathematical puzzles that need to be solved to solve a block
Digital Signatures
A digital signature, similar to your own signature, is used to verify that you are who you say you are. When it comes to cryptocurrencies, digital signatures are mathematical functions that are matched to a specific wallet.
Thus, they function as proof that a specific wallet is actually the wallet it claims to be – essentially, it’s a digital identification of a wallet. By attaching a digital signature to a transaction, no one can dispute that that transaction came from the wallet it purports to have come from, and that wallet can’t be impersonated by another wallet.
Digital signatures use cryptography for wallet identification and secretly match the public and private key of a wallet. Your public key is basically your bank account number, while your private key is the pincode. It doesn’t matter if people know your bank account, because the only thing they can do with it is deposit money to your account. However, if they know your pincode too, you can have a real problem.
In blockchain, the private key is used for the encryption of transactions, while the public key is used for the decryption. This is possible because the sending party is the one responsible for a transaction. The sending party encrypts the transaction with their private key, but this can be decrypted with the recipient’s public key because they only need to verify that it was indeed you who sent the message. If the sending party’s public key doesn’t work to decrypt the transaction, then the transaction isn’t from that wallet.
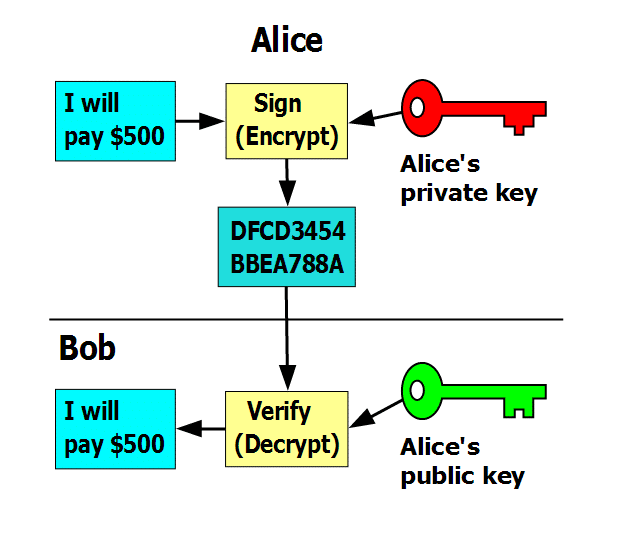
In this system, the public key is distributed freely and is paired secretly to a private key. It is not a problem if a public key is known, but the private key must always be kept a secret. Even though the two are paired, calculating someone’s private key based on their public key is computationally so challenging that it’s financially and technically infeasible.
Protecting the key is a main disadvantage of this method. If others learn your private key, they can access your wallet and make transactions with it, which actually happened in the Bloomberg blunder when a reported accidentally showed his private key on TV.
Related: How to Secure Your Cryptocurrencies
Concluding Remarks
The cryptography that is used for blockchain technology has a lot of different layers to it. This article explores the basics of cryptography and its usage for blockchains, but there is much more technical depth to it. On this website you can learn everything there is to cryptography, for free! If you are more interested in an in-depth overview of the specific cryptographic methods used in blockchain technology, this article can be very helpful to start with.
What’s important to understand about the relationship between cryptography and blockchain technology is the protection and security cryptography provides. It allows for a trustless system in which parties do not have to trust each other because they can place their trust in the cryptographic methods used.
Since the emergence of Bitcoin in 2009, cryptographic protection of the blockchain has withstood all attempts at data-tampering, and there have been many. Moreover, new cryptocurrencies are implementing even more secure methods of cryptography, some of which are already quantum-proof and thus protected from potential future threats.
Without cryptography, there could be no Bitcoin and no cryptocurrency, period. Amazingly, it’s a scientific method invented thousands of years ago that keeps our digital assets safe and secure.