People value their privacy, especially when it comes to financial transactions. Others, such as tax authorities, law enforcement, authoritarian governments or simply hackers, want to know who’s transacting with whom and for what purpose, and often want to maintain some form of control over the process or influence it.
Whatever the rationale for or against privacy, the opposing forces at play create typical cycles of innovation: the need for anonymity creates new, innovative ways to protect privacy, which in turn results in innovative approaches to break the privacy, in turn leading to further privacy enhancing innovation … and so the cycle continues.
Bitcoin, the granddaddy of cryptocurrencies, was originally devised as a currency for peer-to-peer payments without having the need for a central authority. Without a central authority that can monitor, control, some would say spy, on the transactions and the parties involved, it was (and still is) hailed or feared by many as a powerful privacy preserving tool to conduct transactions.
However, it has been recognized that Bitcoin transactions are vulnerable to a range of attacks to break privacy.
As a result, several alternative cryptocurrencies have been developed with the focus on enhancing the protection of the privacy and anonymity of transactions. Spectrecoin (XSPEC) is one of these privacy-focused coins, which offers a well-rounded set of advanced privacy features.
Despite its technical excellence and a roadmap with very interesting innovations, this coin is still little-known outside a small community of privacy experts and enthusiasts, thus presenting an interesting opportunity for investors.
Setting the Scene
In order to appreciate the technical features of XSPEC, we need to briefly remind ourselves of the basic elements of a generic peer-to-peer transaction with a cryptocurrency, such as Bitcoin. In this, I will focus purely on the privacy-relevant components and processes.
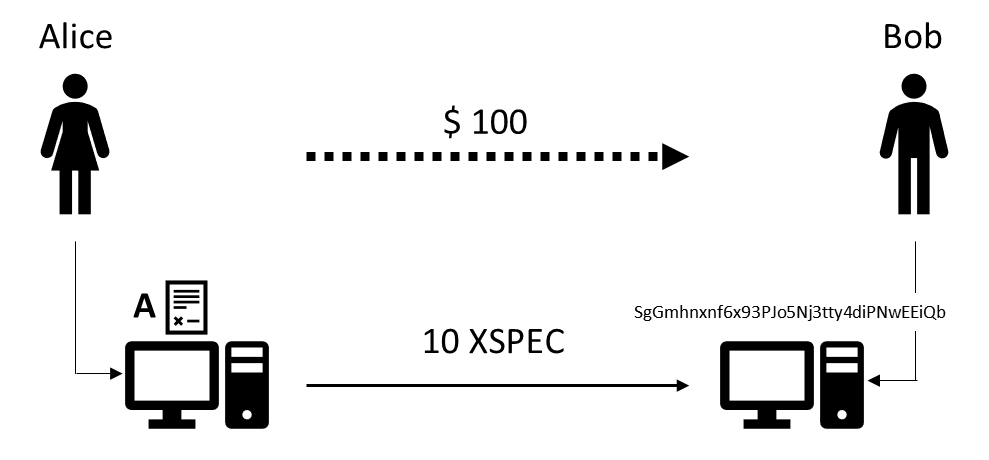
Let’s introduce Alice and Bob. Alice and Bob are the prototypical cryptocurrency users wanting to engage in a transaction. Alice wants to send Bob USD 100, and to preserve the anonymity of the parties and the privacy of the transaction, decides to send 10 XSPEC, the equivalent of USD 100 at the time of the transaction.
So, how does this transaction with cryptocurrencies work and what can go wrong without the privacy features XSPEC offers?
Once Alice and Bob have their electronic wallets set up from which to send and receive payments, Bob first announces the electronic address of his wallet for Alice to send the money to. Alice, using Bob’s address, initiates the payment and signs the transaction with which she declares authenticity. To sign the transaction electronically, Alice includes her cryptographic key. Since there is no central authority to perform the verification, the transaction is distributed among a network of thousands of nodes—each of which participates in a game where the winner verifies the transaction and receives some XSPEC for the effort.
Using Alice’s key, the nodes validate the transaction, while at the same time the underlying cryptography prevents anyone from making alterations. Once the transaction is verified, it will be recorded on the blockchain which is a distributed ledger containing every single transaction since the inception of the cryptocurrency. This blockchain is necessary to ensure proper working of the payment system without a central authority. And by recording on the blockchain, the payment is conceptually debited to Alice’s and credited to Bob’s account represented by the respective addresses of their electronic wallets.
Vulnerabilities and Attacks
Welcome Eve to the scene. Eve, a sophisticated, powerful adversary with unlimited means, wants to learn as much as possible about the transaction and the individuals involved. What are the vulnerabilities and how can they be exploited by Eve?
With the current state of technology, brute force attacks, such as trying to break Alice’s cryptographic key with which she signed the transaction, is not a viable approach. Indeed, to break a commonly used key (AES 128-bit), it would take the most advanced super-computer of today 1.02 trillion years.
So, Eve has to be smarter. The main source of vulnerability in payments with cryptocurrencies that she can exploit rests on one of its most innovative and critical elements: the blockchain itself, and the fact that every single transaction is transparently and permanently recorded on it.
Exposing Alice
As illustrated previously, Alice signs the transaction with her key to provide authentication. This key is like a fingerprint—it can be used to identify the owner.
To be more precise, imagine a crime scene where Eve pulls a fingerprint from an instrument of crime. Eve needs now to compare it to fingerprints from other crime scenes. If she can make a match, Alice’s days are counted.
In the crypto world, the transactions recorded on the blockchain are analogous to the set of “crime scenes” (of course, I am in no way implying that transactions are necessarily illegal). By looking through the blockchain of all the transactions ever conducted, Eve can identify where Alice’s key has been used before. If just a single one of these transactions can be associated with Alice, Eve has succeeded to expose Alice.
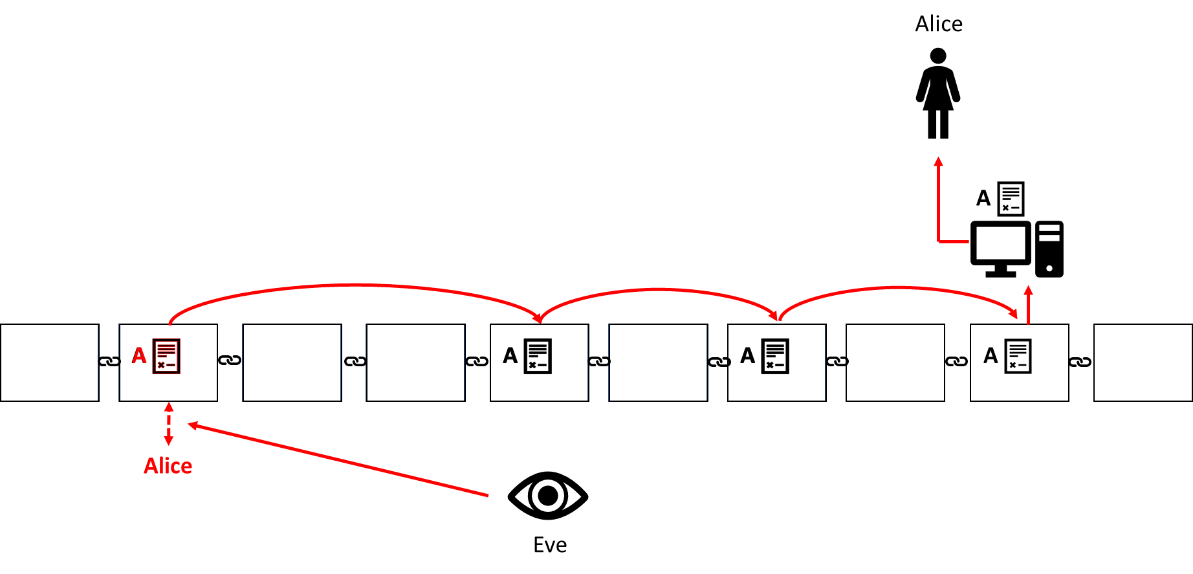
For instance, if Alice used the key to make a purchase at an online merchant where she needed to provide her contact details, or if, in order to exchange her crypto against fiat money, she made a transfer to a cryptocurrency market that required her details for KYC (know-your-customer) purposes, her real-life identity can be traced. Furthermore, if Alice is regularly involved as a party in a chain of transactions, tracing the chain can be used to identify Alice.
Exposing Alice using such type of data analysis on the blockchain is by no means an easy exercise. Given the number of users and transactions—at the time of writing, Bitcoin has about 320 million transactions on the blockchain and the average number of addresses used per day is about 500,000—this type of attack requires significant effort and capabilities which only somebody as powerful and dedicated as our Eve can afford.
On the other hand, Eve could have simply posed as one of those online merchants, or otherwise might have entrapped Alice to send a payment to Eve and thereby revealing her key. And once Eve can associate the key with Alice, all past and future “crimes” of Alice will be recognizable to Eve.
Protecting Alice with XSPEC: Ring Signatures
The problem to solve is obvious: repeated use of Alice’s public key recorded on the blockchain is a vulnerability that can be exploited to expose Alice.
There are different ways to tackle this vulnerability. One is to confuse any potential analysis by using intermediaries, such as a mixing service, between Alice and Bob. Unfortunately, if Eve manages to compromise any such intermediary, she can again get ahead of Alice.
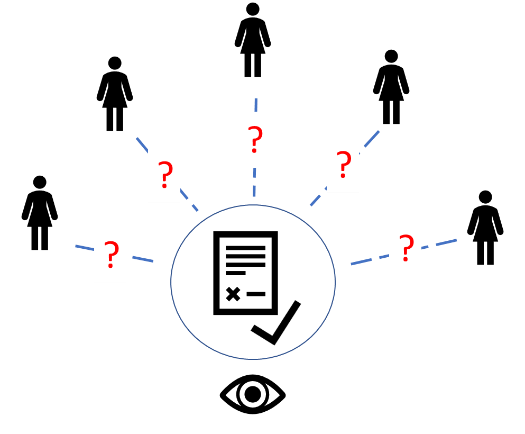
XSPEC implements a more direct approach. With XSPEC, instead of using Alice’s key to sign, each transaction appears to be signed by one person out of a randomly selected group of people, whereby there is no possibility to determine who exactly provided the signature.
With these so-called Ring Signatures, all Eve can do is to verify that the transaction is authentic and determine that somebody in the group has signed, but will not be able to identify the individual who originated the transaction. Plus, given that the group of potential signatories is redrawn at random for every transaction, any chain analysis or more advanced statistical analysis also cannot break the anonymity of Alice.
Exposing Bob
Beaten by XSPEC’s Ring Signatures, Eve now turns her eyes to Bob. Similar to Alice and her key, Bob’s identity becomes vulnerable through revealing his wallet address which Alice needs to send payments to. Even if Bob manages to communicate his address to Alice secretly without being intercepted by Eve, the blockchain records of the transaction expose Bob’s identity to similar types of correlation analysis as mentioned in the case of Alice.
Protecting Bob with XSPEC: Dual-Key Stealth Address
We need an approach in which Bob can announce his address, yet payments can’t be traced back to him. That’s what XSPEC achieves through Dual-Key Stealth Address (DSKA). The name of this method is somewhat misleading, as Bob actually can display his address to everyone to see.
The clever bit about DSKA is that Alice or anyone else wanting to send a payment to Bob can pick up Bob’s address and create a new proxy address for every new transaction. Since only this proxy address is recorded on the blockchain, Eve will not be able to correlate Alice’s payment to Bob, even if Alice and Bob continue to be in business together.

This “magic” is achieved by Bob creating different keys to view transactions and to spend the amount included, and by Alice including relevant meta-data in the transaction itself that only Bob can decipher.
It seems Eve is outmanoeuvred, but is she really?
Exposing Alice and Bob the Sneaky Way
Eve does not give up that quickly, but her task has certainly become significantly more difficult since Alice and Bob started to use XSPEC. So what else can she try?
While Eve has given up identifying the parties to transactions in XSPEC, she still could try to trap Alice and Bob. For instance, if by clever social engineering or other smart manipulation Eve manages to convince Alice to send Bob a very specific, unusual amount—say exactly 23.4389276609823 XSPEC—then as soon as she observes this amount on the blockchain, Eve has evidence that Alice and Bob interacted.
Similarly, if Alice repeatedly sends Bob a specific, identifiable amount that Eve can correlate to service payments, for instance, by observing the amounts transacted on the blockchain, she can draw conclusions about the service provision, potentially leading her back to Alice and Bob. The problem is clear: the amount transacted being visible on the blockchain presents a vulnerability that can be exploited.
Before looking at how XSPEC solves the transaction amount issue, let’s consider other means with which Eve can catch Alice and Bob.
One aspect we have not yet considered is the medium Alice and Bob have chosen to do the transaction—the Internet. Every communication any Internet user is engaged in, be that email, chat, browsing, or cryptocurrency transactions, must be translated from the high-level abstraction of a user-understandable application all the way down to bits and bytes, and ultimately electronic signals which the computer and communication equipment understands and can execute.
At one of these lower levels, each device on the Internet is uniquely identified by its IP address. Whereas the transaction between Alice and Bob might be unbreakably encrypted, their IP addresses are still used in every communication and thus can be intercepted by Eve using traffic analysis.
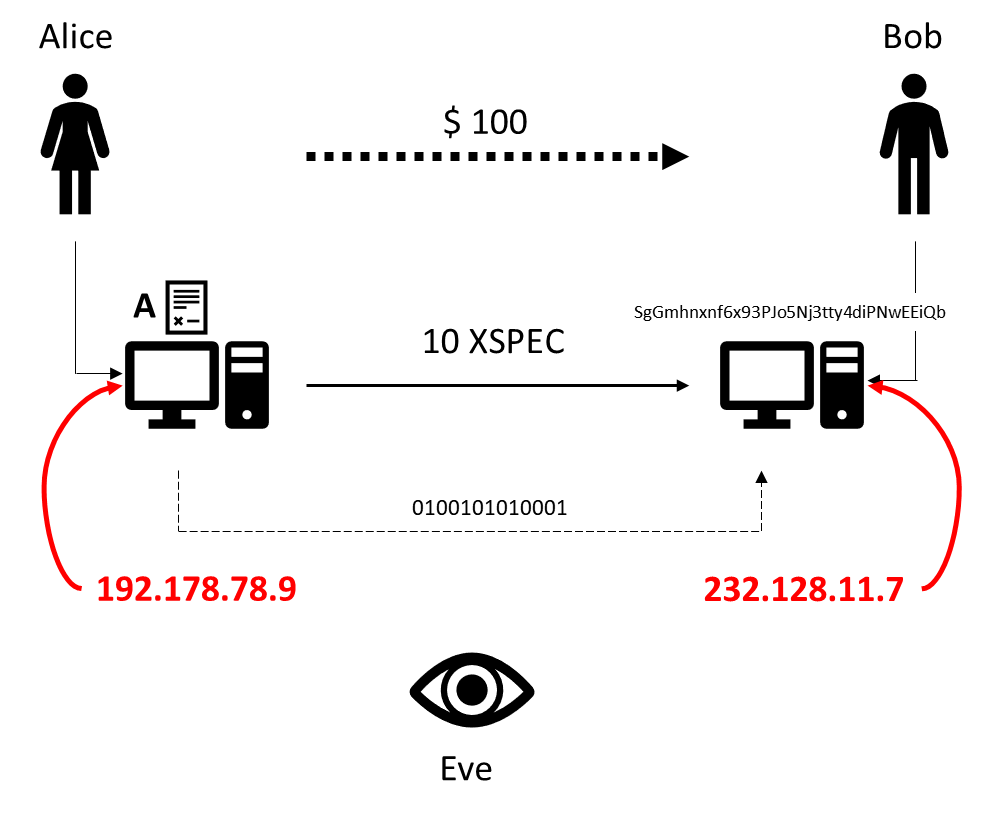
Another vulnerability worth exposing is not related to technology, but to the human element responsible for the technology. Wherever humans are involved, Eve can compromise the entire system by putting pressure on the individuals involved or infiltrating the system itself.
Protecting against Sneaky Attacks with XSPEC: Splitting and Tor with OBSF4
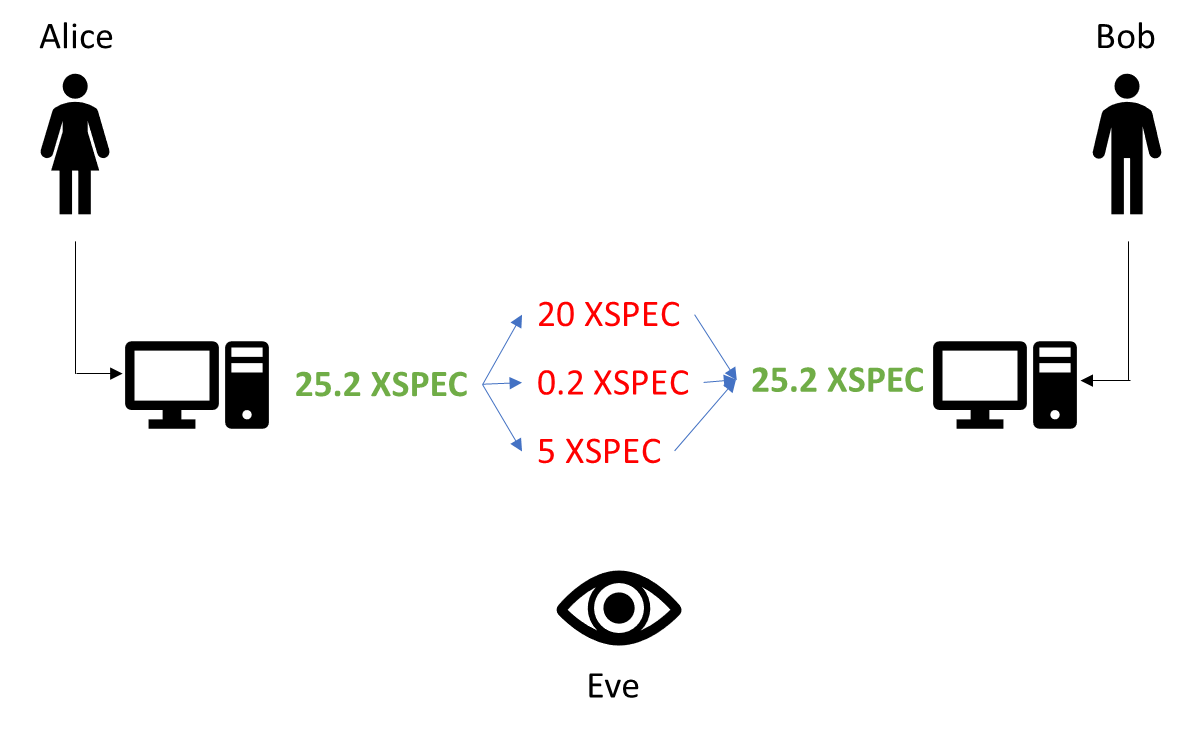
Let’s look at how XSPEC counters the remaining vulnerabilities. To make Eve’s life even harder than it already is, XSPEC does not use the original amount in the transaction but splits the transaction into several tranches, each containing varying amounts summing up the original total of the transaction.
On the receiving end, the Spectrecoin wallet then puts the various pieces together, without Bob ever noticing this piece of magic. On the blockchain, only the tranches are visible which, combined with Ring Signatures and Stealth Addresses, make it impossible for Eve to learn anything about the transaction.
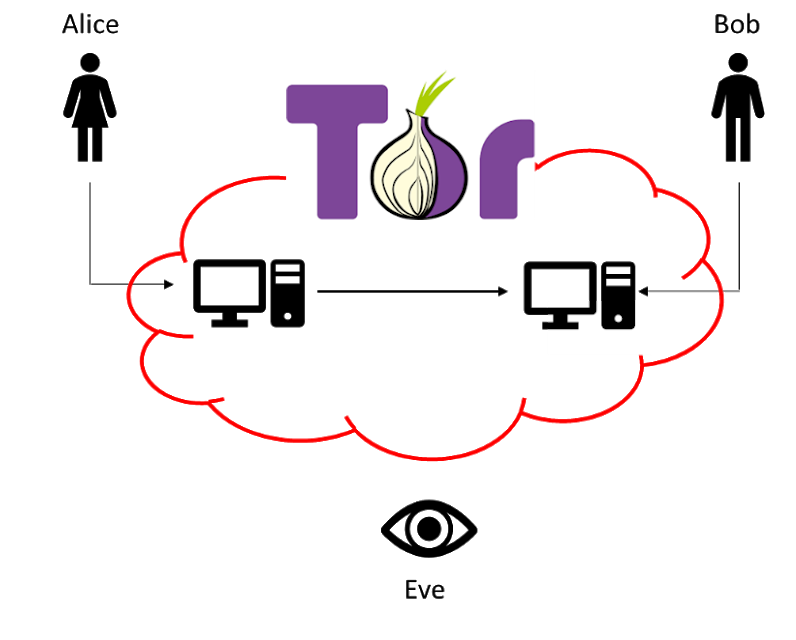
What about the IP address? Here XSPEC leverages natively on the Tor system which is basically a secure network on top of the Internet. Communication packages in Tor are bundled to include only the details of the next relay station transporting the package forward to the receiver. Any attempt to analyse the Internet traffic on the Tor network would thus not be able to identify the sender and receiver address.
One often overlooked problem here lies not in the Tor network itself, but with the communication at the boundary between the normal Internet network and the Tor network. For instance, when Tor is used to anonymously browse Internet sites, the communication remains anonymous until the Tor network is exited, and the normal Internet resources are accessed. At these so-called exit nodes the Tor communication packages are mapped back into normal Internet traffic and thus the IP addresses become visible again.
Whereas many privacy coins can leverage on Tor for communication, the wallets or end-points are on the normal Internet and thus are vulnerable to attacks on the exit nodes. XSPEC has native Tor integration, which means the Tor wallet itself is part of the Tor system, and thus the communication never leaves the Tor network making XSPEC unaffected by compromised exit nodes.
It is worth mentioning that, given the level of IP level anonymity Tor provides, some authoritarian countries are blocking the normal Tor traffic. Tor can circumvent such efforts to be blocked by offering OBFS4 as a pluggable transport, which basically makes Tor communication indistinguishable from normal Internet traffic, and thereby rendering useless any blocking attempts. XSPEC can leverage on OBFS4 and thus make the coin globally accessible, without compromising its Tor-specific privacy.
What’s Ahead?
The roadmap for Spectrecoin has two particular features that are privacy-relevant. At present, XSPEC transactions are public by default and the private, secure transactions are available as a choice. The challenge with this is that if Alice moves 50 XSPEC from her public to her private account, and then submits the transaction securely to Bob who then immediately moves the 50 XSPEC from his private to his public account, these movements between public and private accounts can be observed and potentially be used against Alice and Bob. To mitigate this risk, XSPEC will thus make private accounts and transactions the default in a future version.
The second feature relates to staking. While the Spectrecoin wallet is kept online it becomes a validating node in the network, and in return is rewarded a certain amount of XSPEC relative to the amount of XSPEC kept in the wallet. This process called staking requires the wallet address to be public and the rewards are visible on the blockchain. Version 2.0 of the Spectrecoin wallet, expected to be released in Q2 2018, will include innovative stealth staking that will hide even the staking amounts, to achieve complete, comprehensive privacy in XSPEC.
Even without these enhancements from the roadmap, for the moment, it seems that Eve is defeated. And indeed, the privacy features in XSPEC makes this coin one of the most advanced, well-rounded privacy cryptocurrencies available. Whether you are Alice or Bob, or anyone else valuing privacy in cryptocurrency transactions, Spectrecoin is worth your serious consideration.
Related: The Top 50 Cryptocurrencies