The online advertising industry is currently in limbo, plagued by inadequate and inert website content monetization mechanisms and rampant privacy-invasive ads, distracting users from intended content and harming website design continuity. Ad blockers have become the norm, and visitors click away left feeling uneasy, unfulfilled, and vulnerable, while publishers lose viewership and, ultimately, revenue.
Enter Oyster Protocol, a “true two-birds-one-stone proposition,” bridging the gap between content consumers and content publishers.
Although Oyster’s ICO left much to be desired in terms of finances, raising only 250 ETH and casting Oyster CEO and chief architect Bruno Block into debt, Oyster has since rallied and positioned itself at the forefront of:
- Decentralized data storage
- Website monetization
Built on the IOTA Tangle and Ethereum blockchain, Oyster’s no-nonsense, straightforward single line of code enables website visitors to contribute a portion of free GPU and CPU power – allowing them to store user files on an anonymous and decentralized ledger – and offers a practical solution to curbing the broken and invasive online advertising industry.
Before diving into several key reasons why you should keep an eye on Oyster Protocol in 2018 and what it aims to accomplish, you should first:
- Open up your browser
- Surf the Internet as you’d normally do
- Take note of how many times you are asked to disable your AdBlocker in order to view content
Additionally, if you’re wondering what some of the benefits of decentralized data storage are and the current problems afflicting traditional cloud storage, you can read about it in our write-up about Sia.
Below are 5 reasons why Oyster Protocol is worth keeping an eye on while the market is down.
1. Oyster “Tangles” With IOTA and Ethereum
Combining Ethereum’s smart-contract framework with the IOTA Tangle’s distributed data retention ledger and Proof-of-Work (PoW) mechanism, Oyster Protocol employs a unique method for protecting data and incentivizing users to maintain the network.
IOTA Tangle
Oyster Protocol’s network nodes use the IOTA Tangle as a third-party broker, negotiating PoW performance, compensation, and completion, all while storing uploaded data across a distributed ledger, ensuring increased transaction speeds, and decentralized and attack vector-resistant data storage.
Ethereum Smart Contracts
The native tokens of Oyster Protocol, Oyster Pearls, are produced by Ethereum contract technology, activating distinct token attributes propelling Oyster’s functionality such as burying Oyster Pearls containing Ethereum address private seed keys and locking them in a slow-release state.
Because the Oyster Pearls embedded in the data map with private seed keys of the Ethereum address have no actual ETH for Gas (needed to generate the transaction), a collaboration of nodes is required for a successful transaction and extraction of the “treasure,” a.k.a. the data.
Both functions create one giant “treasure hunt” as one node buries Pearls while another searches for them, thus eliminating potential altruistic actors while retaining data integrity.
So, How Do Tangle and Ethereum Come Together?
Simply put, website visitors (web nodes) contribute free GPU or CPU space to search via PoW for Oyster Pearls, tokens defining the contents and structure of the data file and enabling functionality, buried (as is the case with oysters) in encrypted data maps of uploaded files.
Once located, transaction data is then reattached to the Tangle by a network device with access to the Tangle (hooknodes), and maintained and fragmented across the topology of Tangle nodes, ultimately preventing irrevocable deletion.
You can learn more about the future of IOTA and the benefits of the Tangle.
2. Oyster Protocol Benefits Both Website Visitors and Owners
Striving for equilibrium through incentives for both content consumers and creators, Oyster’s approach to decentralized data storage and web monetization offers a sustainable and user-friendly web browsing ecosystem by:
- Cutting out coercive and unconscionable advertising platforms
- Providing a simple approach to passive revenue for websites
- Giving the people what they want – an ad-free browsing experience
Benefits for Website Visitors
Succinctly put in their white paper, Oyster squashes the age-old overarching and partisan advertisement paradigm, allowing website visitors to “pay the price of admission whilst not being burdened by off-putting and tangential distractions,” – “paying the price” being spending computational resources to do light PoW, in exchange for no “tangential distractions,” online advertisements.
Here are just some of the risks (and irritations) you open yourself up to by viewing online advertisements:
- Obstructed and interrupted content: Think back to the times you exited a website because the actual content was obstructed by, or so fragmented and interspersed with, ads that reading it was a chore.
- Malware: Even without clicking them, advertisements can be a source of malware and viruses, jeopardizing your personal and financial data. Just ask John McCain.
- Unconsented data collection: According to a 2014 consumer security and data privacy investigation report by the U.S. Senate, seemingly innocuous ads may “trigger interactions with hundreds of other parties that may be collecting information on the consumer as he travels the web.”
- Fraud: In theory, cookies can be used to infer personal information about users, such as a person’s age or even medical condition, enabling criminals to target elderly or young persons with fraudulent advertisements.
Should visitors decide to opt out of spending their computational resources for an ad-free browsing experience, Oyster makes the process very simple, presenting users with an on-screen notice of consent.
However, there’s a trade-off.
Benefits for Website Owners
When visitors decide not to participate in “treasure hunts,” website owners are able to block and limit content, widening the ultimate scope of website financial autonomy. For example, websites could implement a policy allowing 30% of visitors to view content without treasure hunting through PoW.
Although such control may appear to tip the scale in favor of website owners, it’s ultimately geared towards eliminating recurring and expensive subscription fees and of course, advertisements.
Quid pro quo. After all, website owners make certain investments to create, deliver, and obtain original content and host it. Keep in mind that Oyster is an alternative to online advertisements and an economic bridge between producer and consumer.
The Oyster Protocol serves as an indirect compensation model for website owners, who get paid in Oyster Pearls that have been discovered by web nodes, the visitor’s browser providing computational power while “treasure hunting.” Additionally, with money actually flowing back to the presently suffering content creators, they are able to put out higher quality content, and more of it, which in turn entices consistent viewership and computational resources.
For an ecosystem favoring neither websites nor the visitors they serve, Oyster Protocol’s dual incentivization model has the potential to not only unlock “dormant revenue potential” in millions of websites, but to offer solutions for storage, privacy, and browsing dilemmas faced by individuals and institutions.
3. It Only Requires One Line of Code
You’re probably thinking, “Well, the idea sounds noble and it does fill a needed gap in the world of online advertising, website monetization, and data storage. But, is it easy to implement?”
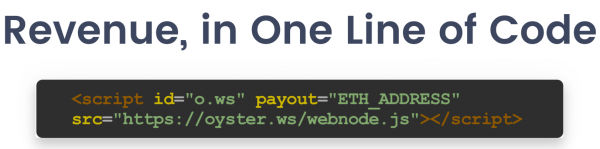
True to its creed, providing users with an alternative online advertising system to the one where online ads obstruct, interrupt, and otherwise detract from website content, Oyster allows website owners to preserve the integrity and continuity of their website with just a single line of code.
Oyster’s single line of code, placed in the website HTML, makes website entry into the world of Pearl simple, and it disburses automatic payment in Pearls to website owners’ Ethereum addresses as soon as a treasure hunting session begins.
In the current blockchain climate, there are numerous barriers to entry for individuals and businesses, and the very thought of needing a special aptitude for programming can put average businesses – and websites – off. Oyster’s single line of code allows businesses to skirt hiring a third-party programmer or exhausting additional resources, and it facilitates entry for those looking to incorporate blockchain into their day-to-day operations.
4. Oyster Employs a Distributed Reputation System
Imagine a bee colony where the weakest and laziest bees are weeded out and disposed of, leaving only the hardest working and most effective. Oyster Protocol implements a similar vetting and cleansing mechanism, known as their distributed reputation system, which tracks the highest performing nodes, assigns them a reputation score, and ensures the network is “performing in the most efficient manner.”
Specifically, broker nodes keep the network running by:
- Processing data
- Uploading files
- Making payments for successful PoW
- Re-encrypting Oyster Pearls
- Retaining the data integrity of the network
When a storage user spends Oyster Pearls to upload a file, top-performing nodes are selected to perform PoW and bury a storage user’s Pearls, which define the contents and structure of the uploaded files, into the blockchain. Oyster’s white paper compares the reputation of broker nodes to eBay sellers, while storage users and web nodes are the buyers.
Just as you’d likely steer clear of an eBay seller with an abysmal feedback rating, web nodes and storage users only conduct transactions with the highest-reputation broker nodes available. Such criteria for broker node selection includes:
- Network latency
- Traffic constraints
- Protocol prohibitions (e.g., using the same node for both upload and verification)
Although the most effective broker nodes aren’t incentivized by high amounts of reward Pearls for performance, Oyster’s economic and reputation pressure requires them to:
- Efficiently and quickly upload files
- Rapidly install data maps and embed and claim Pearls
- Honestly and actually access the real IOTA Tangle after invoking a hooknode
For duly executing such actions, broker nodes enjoy longevity and higher reputation, and, ultimately, a heftier haul of revenue over the long run.
A Built-In Deterrent to Red-Herring Attacks
Additionally, Oyster’s distributed reputation system heavily mitigates the risk of a red-herring attack, where “garbage data” outside the scope of the protocol’s specifications is uploaded by a malicious storage user in hopes of overloading web nodes and tricking them into searching for fools gold, or treasure that doesn’t exist.
However, because web nodes rely on broker nodes (remember the collaboration of nodes mentioned in the section “Ethereum Smart Contracts”?) to receive Genesis hashes, a data encryption scheme, they (web nodes) are able to recognize when broker nodes give out Genesis hashes representing invalid data maps. They subsequently report them, thus ruining a broker node’s reputation and decreasing its future traffic.
5. Oyster Has a Transparent and Active Team
Although Oyster’s lead founder and lead architect Bruno Block has chosen to remain anonymous, Bruno and the entire team consistently publish transparent updates on their Medium, maintain an active GitHub, interact with community members on Reddit, and liaize in various social media channels, such as Telegram and Discord. To note, all other Oyster employees are identifiable by their real names.
In response to why Bruno has chosen to stay anonymous, he stated in a Telegram chat:
Because I [invented] the protocol and that could have political repercussions in the distant future, considering the protocol is the first to enable truly guaranteed storage privacy.
With others stepping in to act as Oyster’s face – cue Taylor French, Oyster’s Design and Communications Director – Bruno’s able to focus on what he does best: code.
When a developer is regularly putting out testnets on time (Testnet A and Testnet B), commenting on the project’s infrastructure, and engaging with the community, it’s worth keeping an eye on and a fundamental reason why Oyster is geared for an exciting 2018 ahead. Transparency and sticking to one’s word goes a long way in an uncertain and volatile industry.
And, if you think Bruno’s anonymity matters: who’s Satoshi Nakamoto?

To learn more about Oyster Pearl, you should check out their website and white paper, both of which provide a good starting point for understanding the Oyster Protocol and its mission.
Additionally, if you’re curious about their 2018 roadmap and developer updates, you can find more info on their Medium, including this video of their live Testnet uploading a file to the Tangle.