Pretend you aren’t staring at a computer screen. You live in a pre-digital world, one where rotary phones and cash registers with pull handles are the norm. The most advanced piece of technology is a brand new audio cassette player you just picked up.
In this world, how would you gather information about someone’s identity? You would talk to their friends, dig through their trash for receipts, maybe even snap a few paparazzi-style pictures from the bushes. In other words, you need physical proximity to the person, as that’s where identity resides.
The digital revolution changed all of that. Connectivity ensures all aspects of our online selves — from social media posts to usernames and passwords — are easy to harvest on a global scale. There’s no need to follow anyone around town. Just task an algorithm to sort through digital details and you can find out all you need to know about anyone.
Events such as the Facebook-Cambridge Analytica scandal have given the public a wake-up call to the importance of online privacy. Managing our digital identities is entirely different from protecting our personal identities. After all, you can’t lock your digital ID in a safe, can you?
Physical and Digital Identities
We carry our personal, physical identity with us everywhere we go. It includes information like height and weight, eye color, gender, skin tone, etc. We can change some of these details, but on the whole our physical identity is what each of us calls “me”.
Identity extends beyond physical features. Your favorite food, the kind of car you drive, your current snail mail address, and other pieces of data are all connected to your identity. These can change over time, but like our height and eye color, they’re part of who we are.
Digital identities are relatively new to the world. They include representations of the above information and a great deal more. Usernames and passwords for all of your online accounts, your search history, social media posts, digital photographs, scanned passport images, and so on. They’re all bound to your digital identity and linked back to you.
A defining factor in digital identities is that they’re permanent. The wall you tagged as a teenager was scrubbed clean years ago, along with any proof that you held the spray can. The same isn’t true for digital data stored on non-local servers, however. Those persist for as long as the company controlling them stays in business.
Digital identities are easy to exploit and highly profitable. An entire industry has sprung up with the sole purpose of making sense of the data trails we leave online. All of these tidbits of information are forever linked to our online identity, and the alarming part is we have no say in what happens to this data once it leaves our hands.
The Depth of Digital Identity
At the end of 2017, an estimated 4.1 billion people had access to the internet, roughly 54% of the world’s population. One thing all of these people have in common is an accessible digital identity.
All it takes is an email address and your digital identity exists. Logging in ties your IP address to that email, making it possible to pinpoint your location. Signing up requires a payment method or your real name, instantly binding the account to your personal identity. Sign up for one mailing list or one website and suddenly your digital identity, which is neatly connected to your physical identity, is in the wild.
A digital identity can encompass a frightening amount of information. On one level it includes every photograph, social media post, and blog comment you’ve ever made. These are optional pieces of data you can choose not to share. Don’t post hundreds of pictures on social media and your digital ID remains minimal.
Another level of data packaged with our digital identities isn’t so optional. These include real-world details like passport scans, physical addresses, Social Security numbers, and birthdate details. We have no choice but to share this information with certain sources. You can’t anonymously sign up for health insurance or open a savings account, for example.
The requirements of identity sharing coupled with the reckless nature of centralized data storage is an easy recipe for disaster. Even the “I have nothing to hide” argument used by critics of the privacy movement crumbles as soon as you take a look at the facts.
You may not have anything to hide in your digital identity, but that doesn’t mean you have nothing worth protecting.
Matters of Privacy and Security
We have to share information online, it’s the only way important services can operate.
Simple sign-ups require an email address. KYC validation requires ID photographs, residential addresses, and other personal details. Sharing identity data lets us have secure accounts, but at the same time, it exposes private information to the digital world.
The problem isn’t the sharing of data, it’s how the data is shared, and what happens to it afterwards.
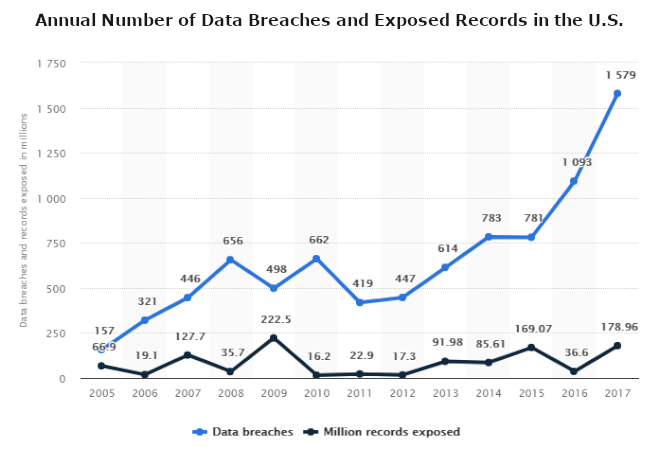
Data breaches and exposed records in the U.S. 2005-2017 — via Statista
One issue with how data is processed is that it’s an all-or-nothing affair. Users can’t choose which details to provide when signing up for certain services. If a bank needs scans of a government-issued ID to verify your name and address, they’ll also know your height, weight, eye color, and more.
Centralized businesses have little incentive to protect collected data, and no incentive to delete it. The information they store is a commodity. Even if the company doesn’t sell or exploit the data, the fact that it exists attracts the attention of hackers.
Digital Identity Management and Control
Most of the problems with digital identity management can be summarized in one word: control.
Currently, centralized companies collect data entered willingly by users in exchange for access to their services. This seems like an ordinary transaction. It’s how brick and mortar businesses have operated for decades, so why shouldn’t online businesses do the same?
This system of data sharing is the digital equivalent of photocopying your driver’s license and giving a copy to every business that needs to see your ID. Anyone would balk at the idea of giving a grocery store clerk a copy of their passport to buy a bottle of wine. Unfortunately, that’s how digital identity is handled these days.
Once you sign up for a service, your personal details are forfeit. A company has control over your digital identity. You can’t protect it, all you can do is cross your fingers and hope nothing goes wrong.
A Solution to Digital Identity Management
This is where projects like SelfKey come into play. SelfKey works using a decentralized self-sovereign identity (SSID). With SSID, individuals retain full control over their data, even while signing documents or sharing details with online businesses.
Instead of passing out copies of your ID to every company that asks, SSIDs provide the digital equivalent of showing your ID once to gain access, then safely stowing it in your wallet.
Let’s say you want to sign up for a cryptocurrency exchange. The account creation process sends users through a rigorous KYC validation program that involves submitting scanned ID documents, then waiting days or weeks to verify your identity. Those documents remain with the exchange long-term, essentially giving the company a copy of your digital identity.
With SelfKey and SSID, the KYC process is faster and far more secure.
To sign up with Exchange X, you first request ID verification through SelfKey’s decentralized network. Notarization takes place using a public key, then you share the trustless confirmation and public keys with the exchange.
Exchange X only gains access to the relevant details needed to create your account, not your entire digital identity. It then uses the public key to complete the onboarding process. No other data is transferred. You remain in full control over your identity at all times.
This simple solution to digital identity management eliminates most of the major issues in online privacy. It prevents businesses from amassing databases of user information. It cuts the risk of data breaches. And it streamlines the sign-up process for services, letting ID owners create bank accounts, join exchanges, or even apply for residency permits using SSID.
Learn more about the SelfKey project and the release of their long-awaited identity wallet.
Digital Identities of Tomorrow
Digital identities are in a precarious position. They represent a massive amount of private data, yet they’re insecure and almost impossible to protect. Giving up control is mandatory in many cases, creating a no-win situation for the general public.
Solutions like SelfKey enable individuals and companies to enjoy complete control over their identity and data. You share what you want, with whom you want, and for as long as you want, all without giving up ownership of your private information.
We have full control over our personal and physical identities. Why should digital identities be any different?
Related: What is SelfKey (KEY)?